UPX Unpacker Plug-in
PE Explorer ships with the UPX Unpacker plug-in, a start-up processing plug-in for unpacking files compressed with UPX by Oberhumer, Molnár & Reiser (see upx.github.io). All versions of UPX are supported, from the obsolete early versions (prior to 0.80) up to the latest 4.0x versions.
In addition, PE Explorer supports for files modified with many UPX scramblers such as Advanced UPX Scrambler, UPoLyX, UPX Lock, and even more: now it supports for Upack and NSPack.
Now you can open files compressed with UPX even without knowing that!
When you open a file with PE Explorer, the UPX Unpacker plug-in detects whether a file is packed with UPX, and then your file will be unpacked automatically. The resulted file will also be saved unpacked. PE Explorer does not re-pack the previously packed files. That is why the original file size may be increased after you save the executable WITHOUT making ANY changes to it in PE Explorer.
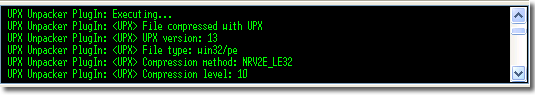
UPX Unpacker displays lines of messages in the bottom log window as follows:
Unpacking Malicious Software
The UPX Unpacker plug-in works on packed malware executables and can handle a file even if it has been packed with UPX and modified manually so that UPX cannot be used directly to unpack the file, because internal structures have been modified, for example the names of the sections have been changed from UPX to XYZ, or the version number of the UPX format has been changed from 1.20 to 3.21. This technique often is used by malware authors to make unpacking and reverse engineering harder.
Previously, you had to run the executable and dump the packed segments right after the executable had been completely unpacked in memory. Now you can open these obfuscated files even without knowing that: your file will be unpacked automatically!
UPX Unpacker attempts to recover a file, even when an original PE file header entry is no longer available after unpacking. Previously, losing the PE file header rendered the executable completely inoperable and unrepairable. Now you have good chances to analyze packed malware executables and extract hidden data.
Write Your Own Custom Plug-ins
The PE Explorer Unpacker plug-ins unpack only files compressed with UPX, Upack and NSPack. Consult the PE Explorer help for the plug-in API: you can write your own custom start-up processing plug-in for crypted files handling or unpacking the packed files. Using the Plug-in Manager, you can set priority of executing plug-ins: Menu Tools | Plug-in Manager.
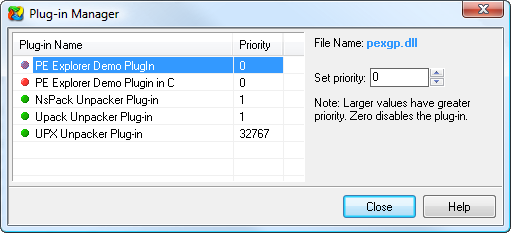
Within the PE Explorer directory there must be a subdirectory named PLUGINS. All plug-ins (DLLs) should be placed in this folder.
The plug-in API will be extended, therefore when writing custom plug-ins, it is important to pay special attention to the remarks made in the description of Functions and Types (see the product help file), and abide by them. Following these guidelines will keep your coding compatible with future versions of PE Explorer.
Get Started with a 30-Day Free Trial
Download PE Explorer and start exploring your applications now.
 PE Explorer runs on all versions of Windows, from Windows 95 to the latest version of Windows 11.
PE Explorer runs on all versions of Windows, from Windows 95 to the latest version of Windows 11.